Integrating VMware Log Insight with Workspace ONE Access for SSO
Introduction
In this post we are going to explore the easiest way to integrate VMware's Log Insight with Workspace ONE Access for providing SSO both in SP-INIT and IDP-INIT authN & authZ flows.
Prerequisites
For the purposes of this blog post, I will assume you have Log Insight downloaded and installed and at least working in a clean fashion on your network. This means you can browse to your Log Insight FQDN and login with the local admin account without receiving any errors.
The above means the following are also configured correctly and work properly:
- DNS - You can browse to the FQDNs of all necessary items.
- Network Routing - You can reach all IPs and FQDNS of all necessary items.
- NTP - Network Time is properly set and synced on all systems.
- SSL/TLS - Certificates are properly configured on all systems.
- Directories - Security databases such as LDAP/AD and others are properly configured and reachable.
Integration of Log Insight with Workspace ONE
Background
VMware's Log Insight doesn't utilize SAML or OIDC but rather just an OAUTH authorization token with account validation occurring on Log Insight.
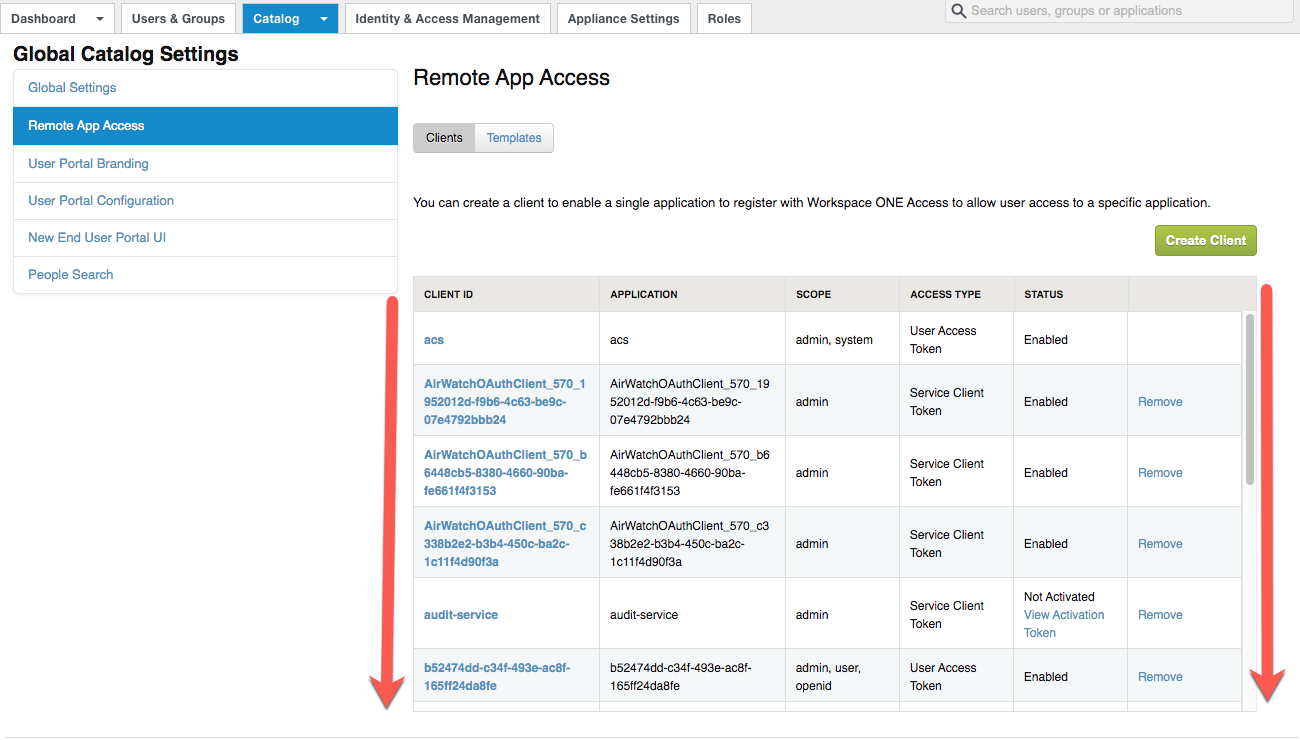
NOTE: Prior to conducting the SP Initialization Flow procedure, if you wish to also create a Log Insight app within your WS1 Access catalog, log into your Workspace ONE Access tenant as an admin, browse to CATALOG → (drop down menu) → Settings → Remote App Access and take a screenshot (or multiple if you need to scroll) as the below process will create a OAUTH2 client for authorization use. The screenshot(s) here will help you identify the new client ID as there will be nothing to indicate the new OAUTH2 client is for Log Insight.
SP Initialization Flow
- Once you can get into Log Insight with the local admin, browse to the Administration tab at the top and select Authentication under the Configuration menu on the left (See screenshot further below).
- On the Authentication Configuration page under the VMware Identity Manager tab, you can enable and set the following:
- Click the "Enable Single Sign-On" switch
- Type in the FQDN for your Workspace ONE Access host (e.g. company.vmwareidentity.com)
- Ensure the API port is set to 443
- Type in the Username and Password for a local Workspace ONE Access tenant ADMIN (suggest using a SUPER ADMIN in the SYSTEM DIRECTORY)
- At this point, click the TEST CONNECTION button
- Set the "Redirect URL Host" to the Log Insight FQDNNOTE: If this is not allowing setting of anything other than an IP address, see this VMware KB and manually setting the redirect target to the FQDN for Log Insight
- If you also wish to still allow Active Directory user logins at the same time, you may also enable this switch
- Click SAVE - if you get any Untrusted Cert popups during this process, click ACCEPT after validation of the certificates

- Now you need to import users from Workspace ONE Access into Log Insight. To do this, browse to the Administration tab at the top if not already there, then under the Management menu on the left, select Access Control. From here you can do any one of the following:
- Create a new local user
- Import an Active Directory user (if AD is already integrated)
- Import a Workspace ONE Access user (either local tenant or AD integrated)
- To import a Workspace ONE Access user...
- Select "+ NEW USER" in the upper left section of the main page
- Change Authentication to "VMware Identity Manager"
- Change the Domain field to match what the user's domain shows as within the Workspace ONE Access tenant (this can be found when logged in to Workspace ONE Access as an Admin on the Admin Console under the Users & Groups tab)
- Enter the user's username value
- Optionally type in the user's email address as well
- Select the type of Log Insight ROLE the user will have
- Click SAVE.
- If validation fails, you may need to backup and adjust what you are entering for domain or username values

- You should now be able to test the SP-INIT flow by browsing (via a different or incognito/private browser window) to the Log Insight login page, selecting "VMware Identity Manager" from the drop down menu, and clicking LOGIN VIA SSO. This will redirect to the Workspace ONE Access tenant for authentication and authorization. Once authenticated to Workspace ONE Access, Log Insight will then authorize the claim so long as the user is imported properly from the Workspace ONE Access tenant.NOTE: No SAAS application resource needs to be created within Workspace ONE Access for the SP-INIT flow to work.

IDP Initialization Flow
As mentioned above, for Log Insight to utilize Workspace ONE Access for authentication, no "Log Insight" application needs to exist in the Workspace ONE Access catalog for OAUTH authorization to function - so long as the user exists within both Workspace ONE Access and in Log Insight. That said, it may be nice for admins to also have a catalog of admin resources to easily authenticate into, so adding a catalog resource is pretty simple to do...but there is one thing needed in order to make this work properly.... the URL which the Log Insight user is redirected to initially when clicking the LOGIN VIA SSO button.
Getting the WS1 Access OAUTH2 Client ID for Log Insight
Using the initial screenshot(s) of the REMOTE APP ACCESS screen where all of the OAUTH Client IDs are listed, compare your screenshotted list with the actual list now and look for the new entry. It will have a SCOPE containing "admin, user, openid" (where most others won't contain "openid"). If you open it, you should see the REDIRECT URI defined as "https://[your_Log_Insight_FQDN]/login" where your Log Insight FQDN is specified.
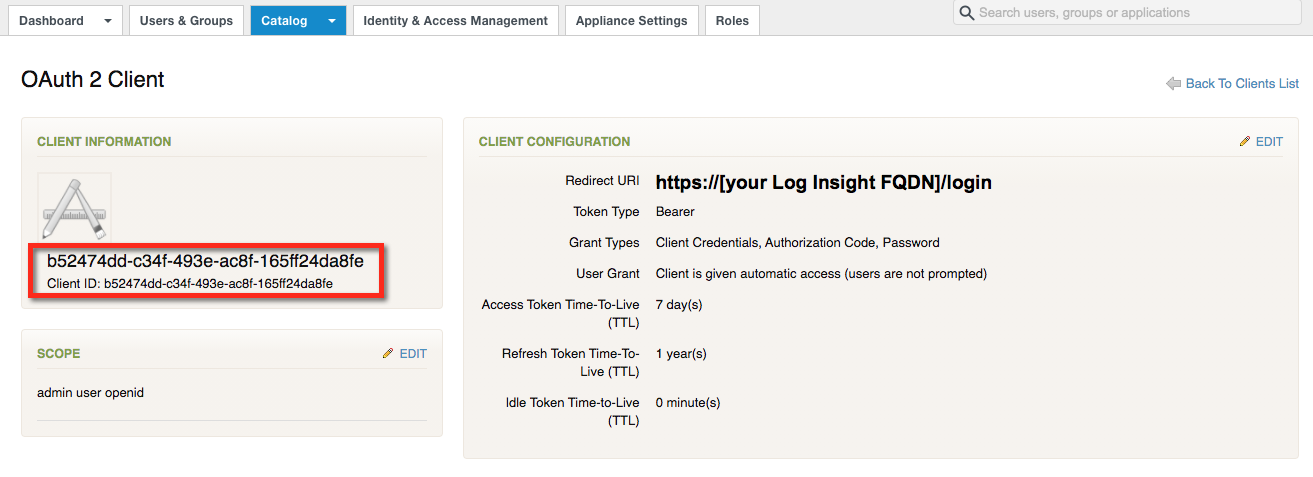
Specifically, we will need the Client ID GUID value (the big, long, alpha-numeric value with 5 segments separated by dashes). Copy the Client ID GUID value to your clipboard or notepad.
Getting the Target URL
Now that we have the Client ID, we need to build the Target URL. This is comprised of a couple of pieces of information:
- The Workspace ONE FQDN
- The Workspace ONE OAUTH2 Client ID for Log Insight (which you setup in the SP-INIT procedure above)
- The Log Insight FQDN
Target URL Template:
https://[your_WS1A_FQDN]/SAAS/auth/oauth2/authorize?response_type=code&client_id=[your_WS1A_LOG_INSIGHT_CLIENT_ID]&redirect_uri=https://[your_LOG_INSIGHT_FQDN]/login
NOTE: Ensure when replacing with actual values, you remove the "[" and "]" brackets.
Target URL Example:
https://test.vmwareidentity.com/SAAS/auth/oauth2/authorize?response_type=code&client_id=b52474dd-c34f-493e-ac8f-165ff24da8fe&redirect_uri=https://loginsight.company.com/login
Testing the Target URL
To test the above URL, simply paste it into a clean browser window (where you are not already authenticate to either Workspace ONE Access or Log Insight). It should immediately redirect you to Workspace ONE Access to authenticate. Once properly authenticated with a user that is imported to Log Insight, you should immediately be authorized into Log Insight.
Creating the Log Insight application with in the Workspace ONE Access catalog
- Login to the Workspace ONE Access tenant as admin and browse to the Admin Console if you are not already logged in.
- Browse to CATALOG → (drop down menu) → Web Apps and click the NEW button.
- Leave the SEARCH field blank. Under NAME, type in a Name, a Description, upload an Icon, and define any Categories for the new Log Insight app. Click NEXT

- Change Authentication Type to Web Application Link and paste in your validated Target URL and click NEXT.

- Now click SAVE & ASSIGN in the Summary screen.

- Define the individual users and/or groups within the Assign screen and click SAVE.NOTE: Defining users here ONLY provides the icon within their personal Workspace ONE Access tenant catalog! It DOES NOT provision the user account within LOG INSIGHT (this still must be done separately).

- Browse to the Workspace ONE Access console as the user(s) defined and see if the Log Insight app appears (for Workspace ONE Access SaaS tenants, user provisioning can take some time).

Conclusion
You should now have SSO from VMware Workspace ONE Access into VMware vRealize Log Insight whether you go directly to Log Insight's FQDN or indirectly to the Workspace ONE catalog!
Next Steps
So now what? Well, let's put Log Insight to use as a SYSLOG server as well as by loading the LI Clients on the On-Premises Workspace ONE Access On-Premises SVAs.
