Mobile SSO for Android Setup with Workspace ONE
Credits to Steve D’Sa over at the identityguy.ca for the original posting. His original article needed to be updated with all of the changes to VMware’s Workspace ONE - including UI and other changes.
Introduction:
There are multiple parts to configuring Mobile SSO when the wizards are not used. One thing to note, the process can seem a bit circular... so there are some things you need to do and then go back and edit to update.
- Configure the Tunnel Client and Export Tunnel Certificate
- Enable the Mobile SSO (for Android) Authentication Method
- Create the Mobile SSO (for Android) Policy Rule
- Create the Android Profile in Workspace ONE UEM
- Add Android Apps and Configure to use Tunnel
- Create the Android SSO Device Traffic Rules
- Edit Android Apps to Use Android SSO Profile (if needed)
- Edit the Android SSO Profile in Workspace ONE UEM to use Android SSO Traffic Rule
Configure the Tunnel Client
When you are configuring Android Mobile SSO, it requires you to configure the Tunnel Client. You do not need to deploy UAG. Its also important to know that Mobile SSO will not work if you have configured another VPN client on the device.
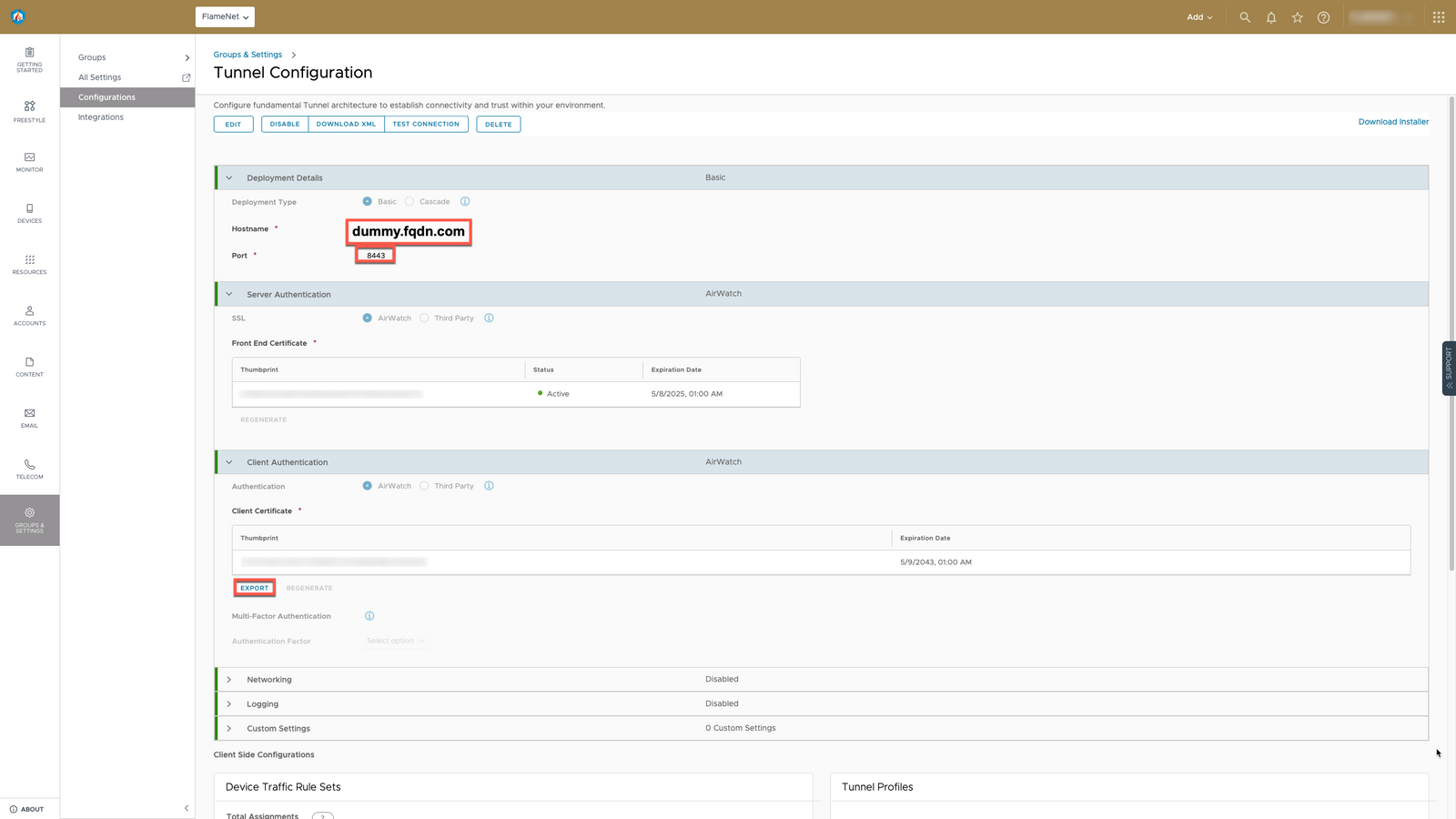
- In Workspace ONE UEM, go to Groups and Settings -> All Settings -> Enterprise Integration -> VMware Tunnel
- Under Deployment Type, select Basic
- Under Hostname, select a dummy hostname. Do Not USE your Workspace ONE Access URL.
- Under Port, use 8443
- Under Server Authentication, use the default AirWatch CA
- Under Client Authentication, use the default AirWatch CA
- Export the certificate.NOTE: You will need to first save, then go back and reload the page to be able to export the certificate.
Enable the Mobile SSO (for Android) Authentication Method
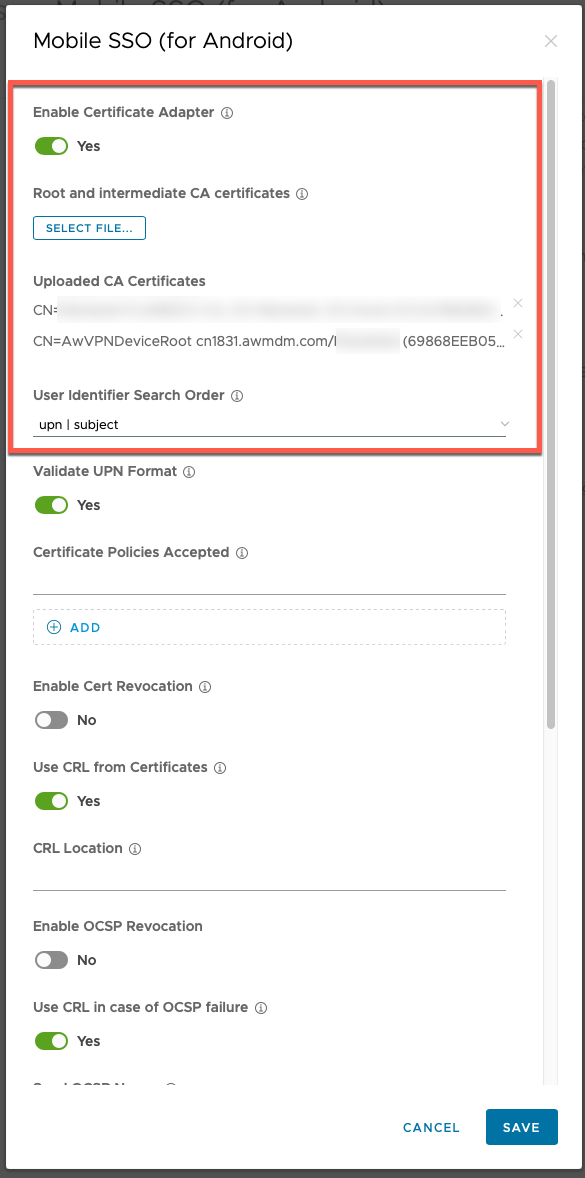
- In the Workspace ONE Access in the Admin Console, go to Integrations -> Authentication Method
- Click edit for Mobile SSO (for Android)
- Enable the Certificate Adapter
- Upload the Tunnel Certificate we just downloaded
- It is recommended if USING AIRWATCH CA (AW SCEP), then under User Identifier Search, select "upn|subject" and if USING ANYTHING OTHER THAN AIRWATCH CA (i.e. MS ADCS), then under User Identifier Search, select "upn|email|subject".NOTE: Take the above "recommendation" with a grain of salt...since....so long as the User Identifier search field contains the value type provided in the certificate (e.g. UPN, Email, Subject, etc.), then whatever search order selected should work. To note, using "upn|email|subject" provides broader support than just "upn|subject"...but if your certificate settings provide email instead of username (or vice versa), then this would dictate which one of those you select first in the search order.
- Click Save
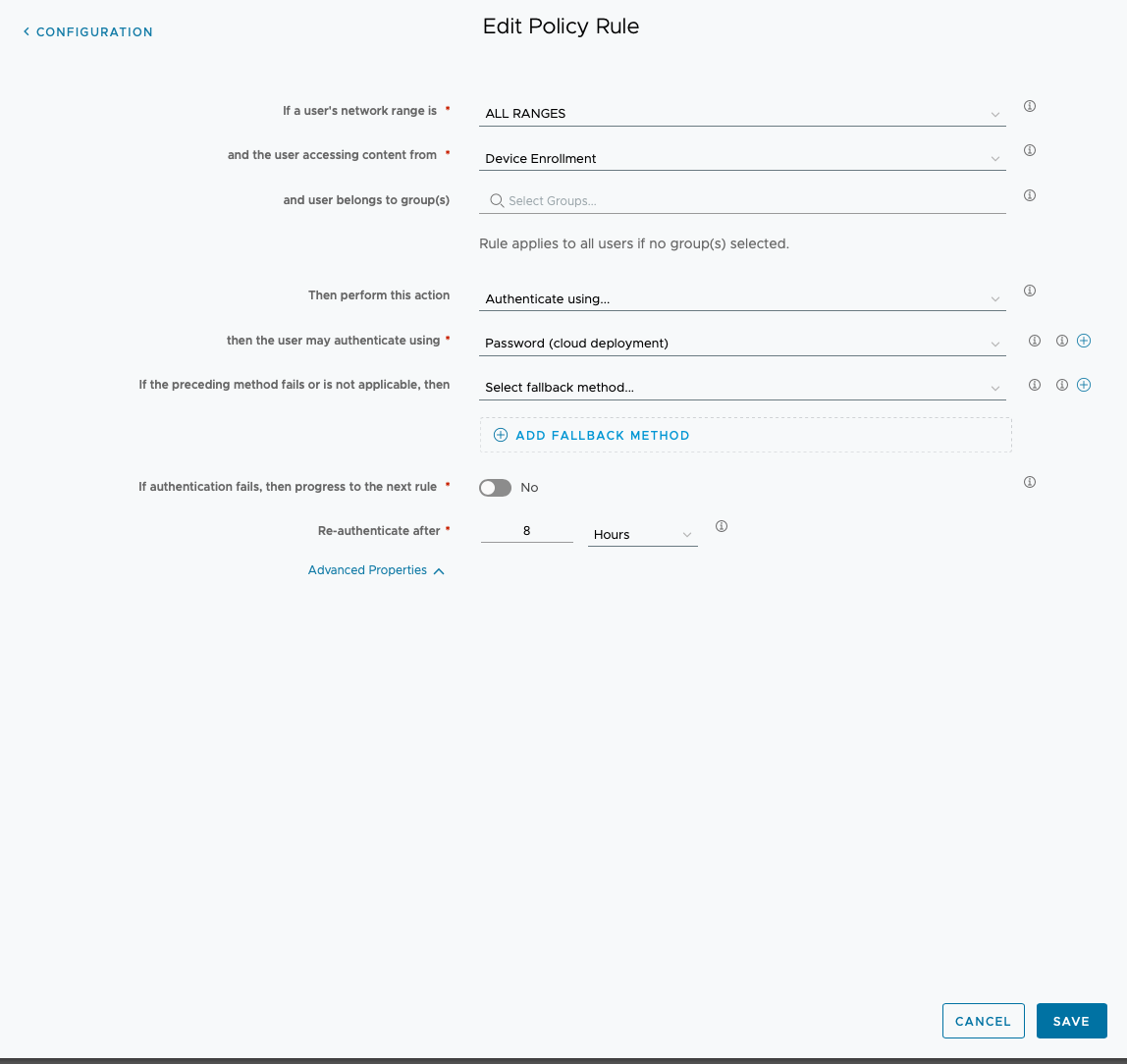
Create the Mobile SSO (for Android) Policy Rule
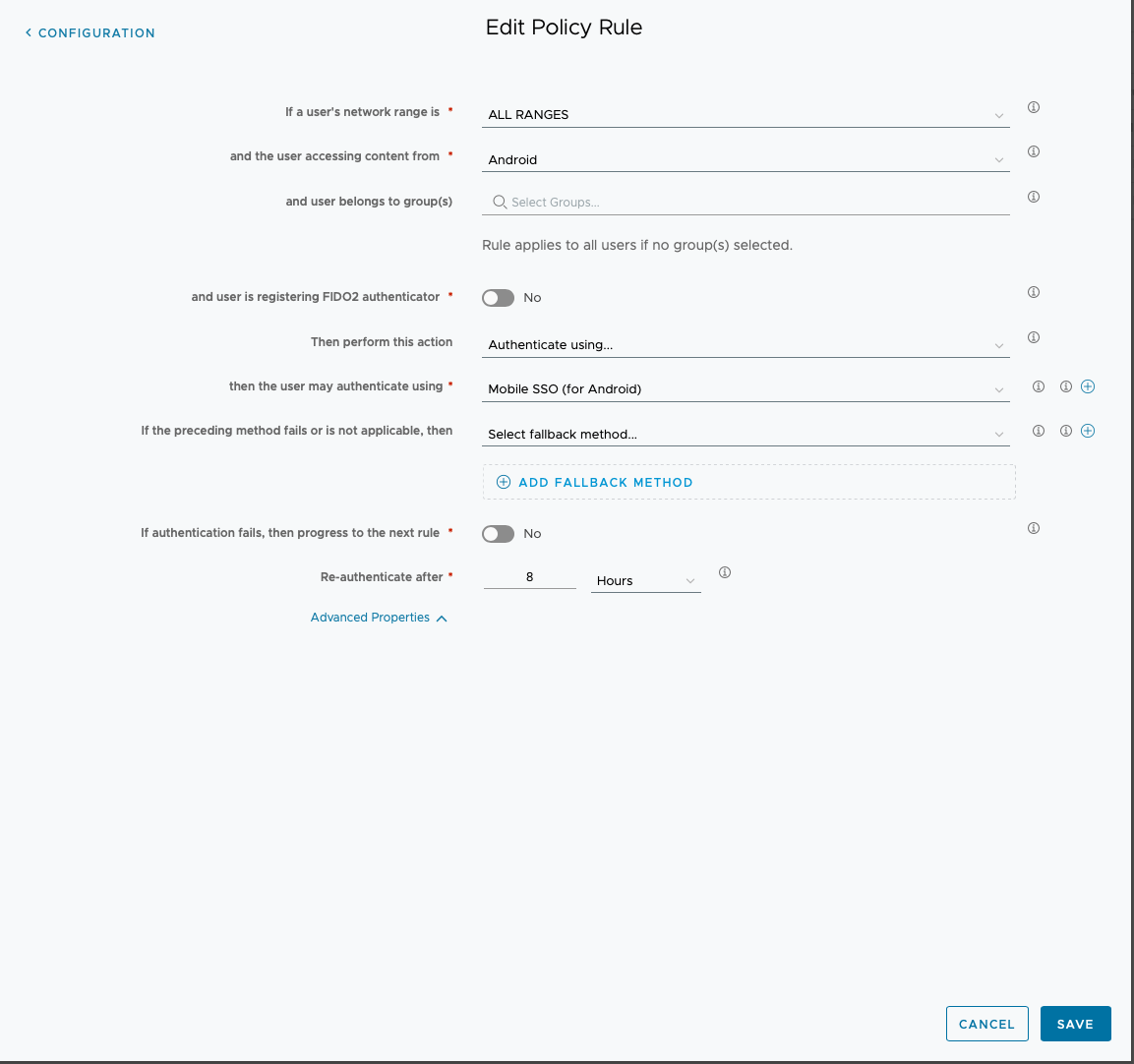
- In the Workspace ONE Access in the Admin Console, under Resources > Policies, edit the default_access_policy_set.
- Under the Configuration section, you will need to add a new Policy rule for Android (Mobile SSO).
- In simplest form, use the following settings:
- Network Ranges: ALL RANGES
- Platform (access content from): Android
- Leave user groups blank
- Leave FIDO2 registration off/disabled
- Authenticate using: Mobile SSO (for Android)
- Click SAVE
- You may also wish to create an ENROLLMENT profile with the following settings. This will allow for BYO-style device enrollment assuming Workspace ONE UEM allows for authenticated user enrollment.
- Platform (access content from): DEVICE ENROLLMENT
- Leave user groups blank
- Leave FIDO2 registration off/disabled
- Authenticate using: Password (Cloud Deployment)
- Click SAVE
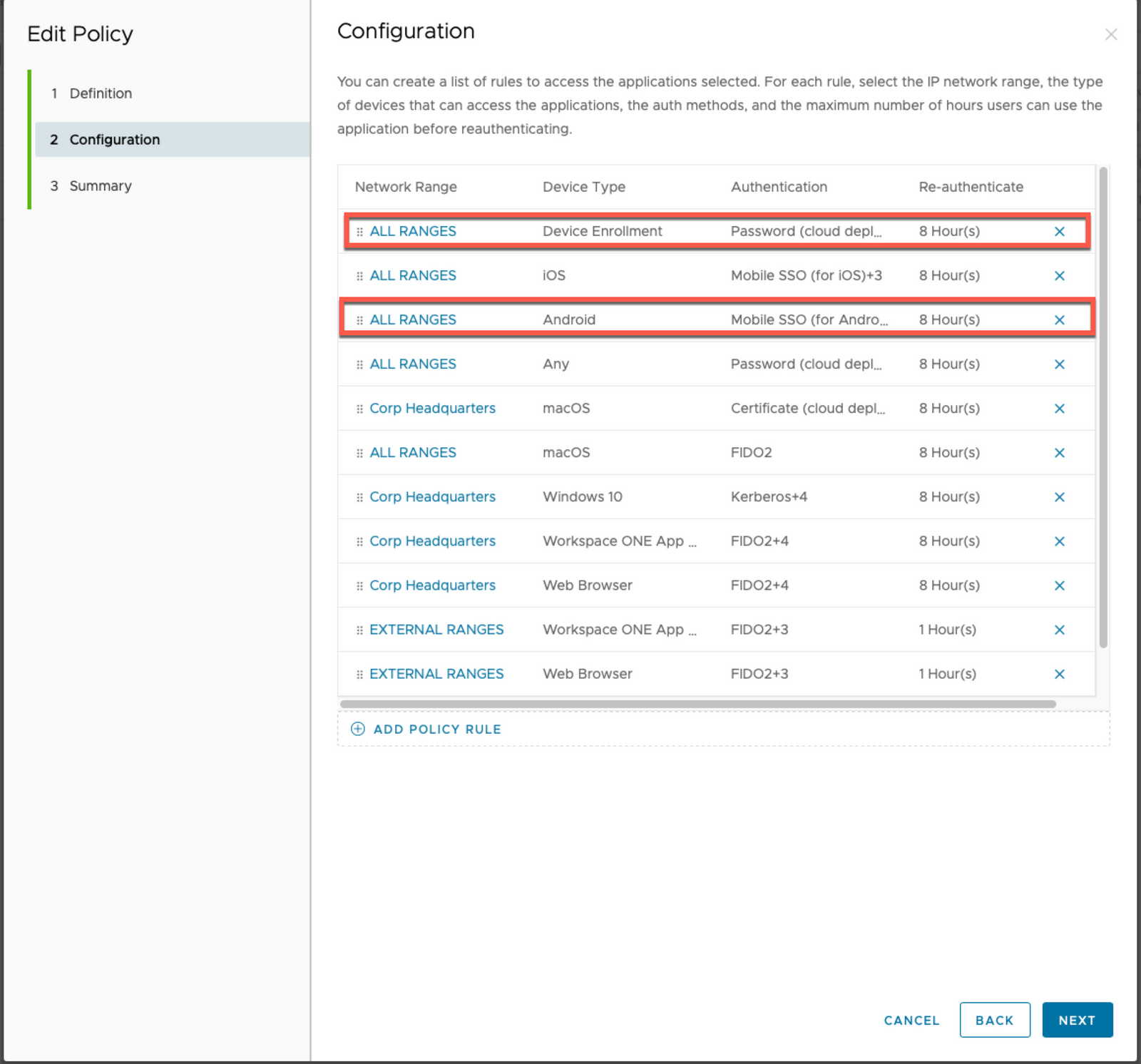
- Order the Access default policy rules so the ENROLLMENT policy rule is first and Android Mobile SSO is under that in some fashion.
- Click NEXT
- Click SAVE
Create the Android Profile in Workspace ONE UEM
- In Workspace ONE UEM, go to Resources -> Profiles
- Click Add -> Add Profile -> Android
- Give the profile a Name (Top left)
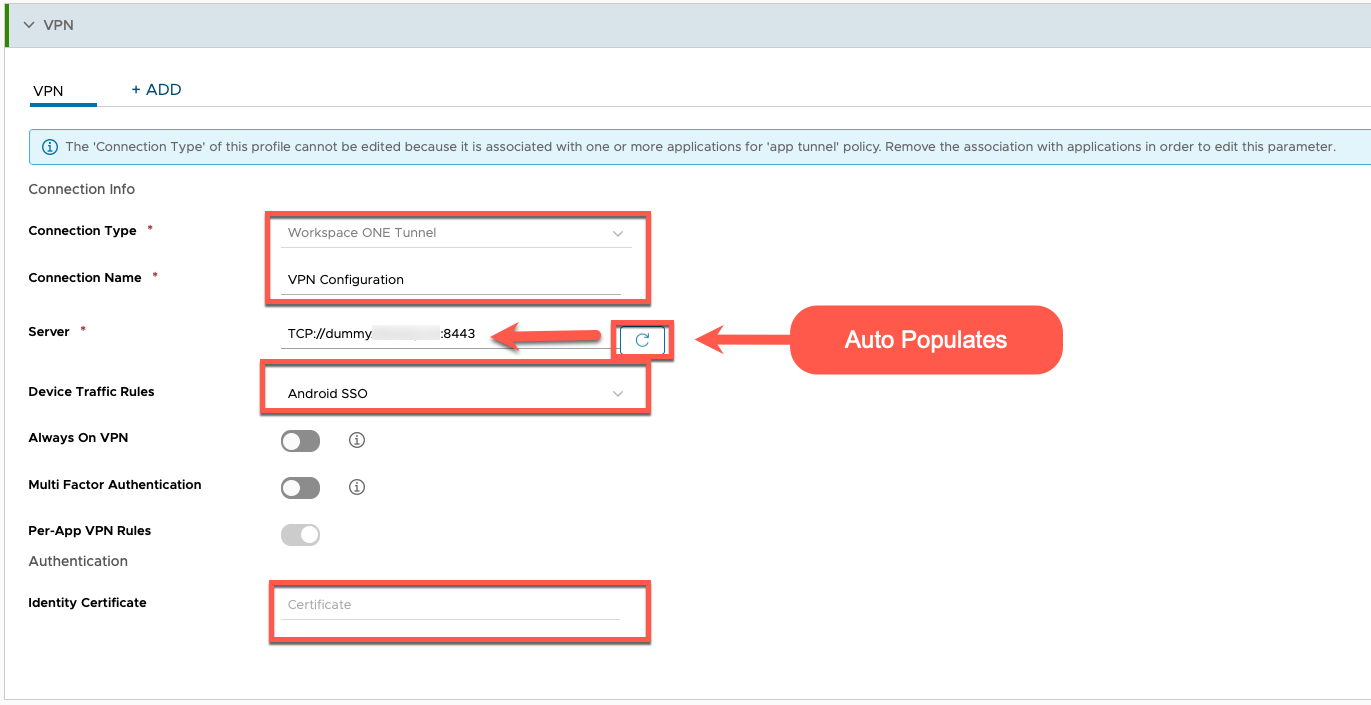
- Under VPN, click Configure
- Ensure Connection Type is Workspace ONE Tunnel
- Ensure Connection NAME is VPN Configuration
- Server will auto-populate to your dummy FQDN defined previously in the Tunnel Configuration section.
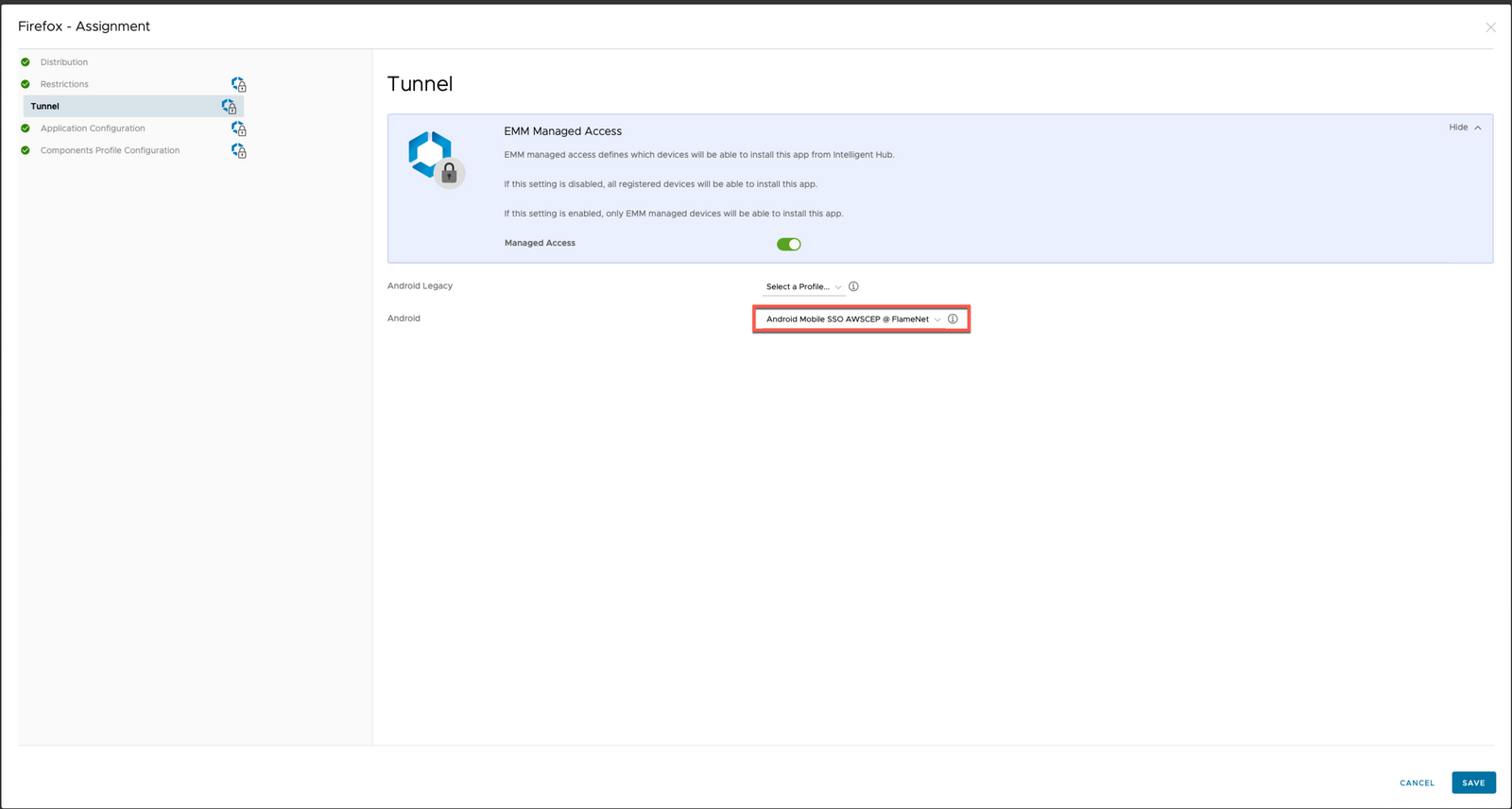
- Device Traffic Rules will say DEFAULT.NOTE: You will want to come back and change this once you have defined Android SSO device traffic rules in order to change this to your Android SSO device traffic rule!
- Click NEXT
- Assign a Smart Group (ie Android Devices).
- Set assignment type to AUTO.
- SAVE & PUBLISH.
Add Android Apps and Configure to use Tunnel
- In Workspace ONE UEM, go to Resources -> Apps -> Native -> Public
- Add three Android applications to start...
- Intelligent Hub
- Tunnel for Android (this will proxy all app traffic on the device to Workspace ONE for SSO).
- Chrome (this will be used by any mobile app you deploy within Work Managed devices in order for mobile apps to do SSO via webclip).
- Name the app distributions
- Set App Delivery to AUTO
- Assign to Android devices (You can go back and modify these later).
- In Restrictions, enable MANAGED ACCESSNOTE: This is technically not required, however doing so will make testing a bit easier for when unenrolling, all managed apps are wiped.
- In TUNNEL settings, select your Android Mobile SSO Profile
- Click CREATE, SAVE, & PUBLISH.
Create the Android Device Traffic Rules
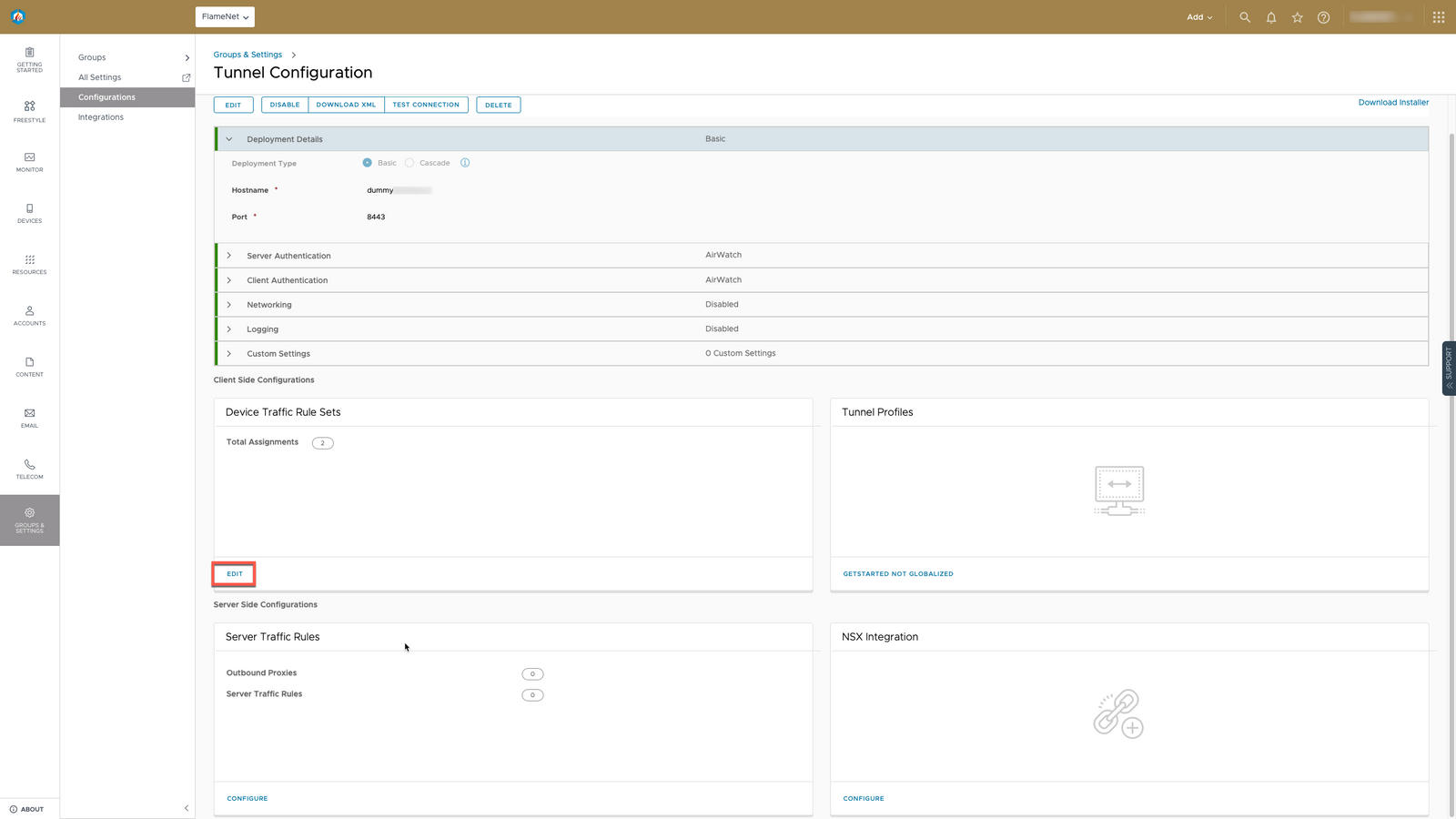
- In Workspace ONE UEM, go to Groups and Settings -> All Settings -> Enterprise Integration -> VMware Tunnel
- Under DEVICE TRAFFIC RULES SET, click EDIT in the lower left corner of that window to edit the device traffic rules.
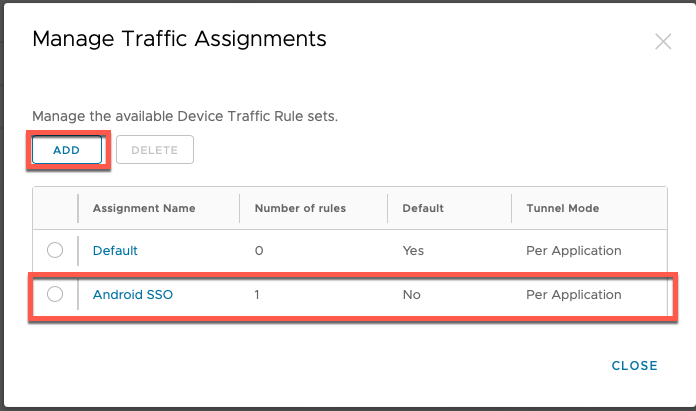
- Click ADD.
- Name the traffic rule Android SSO.
- Set the Tunnel Mode to Per Application.
- Add your Android applications to the first rule.
- NOTE: If you do not see your android apps show in this screen, you need to edit each android app ASSIGNMENT so that the Android SSO Profile shows in the "Android" box under the TUNNEL screen of the app assignment.
- Set the 1st rule to PROXY.
- Define the WEB PROXY value to one of the below based on your tenantExample: Your tenant is https://
.vmwareidentity.com so you will use the 1st certproxy address below - If your tenant is "workspaceoneaccess.com" then your certproxy address will be number 2). - https://certproxy.vmwareidentity.com:5262
- https://certproxy.workspaceoneaccess.com:5262
- https://certproxy.vidmpreview.com:5262
- https://certproxy.vmwareidentity.emea:5262
- https://certproxy.vmwareidentity.asia:5262
- Enter your VMware Identity Manager or Workspace ONE Access tenant URL in the destination box.
- Click SAVE.
NOTE: DO NOT FORGET TO GO BACK TO YOUR ANDROID PROFILE IN WORKSPACE ONE UEM AND EDIT IT TO ADD IN YOUR ANDROID SSO DEVICE TRAFIC RULE!
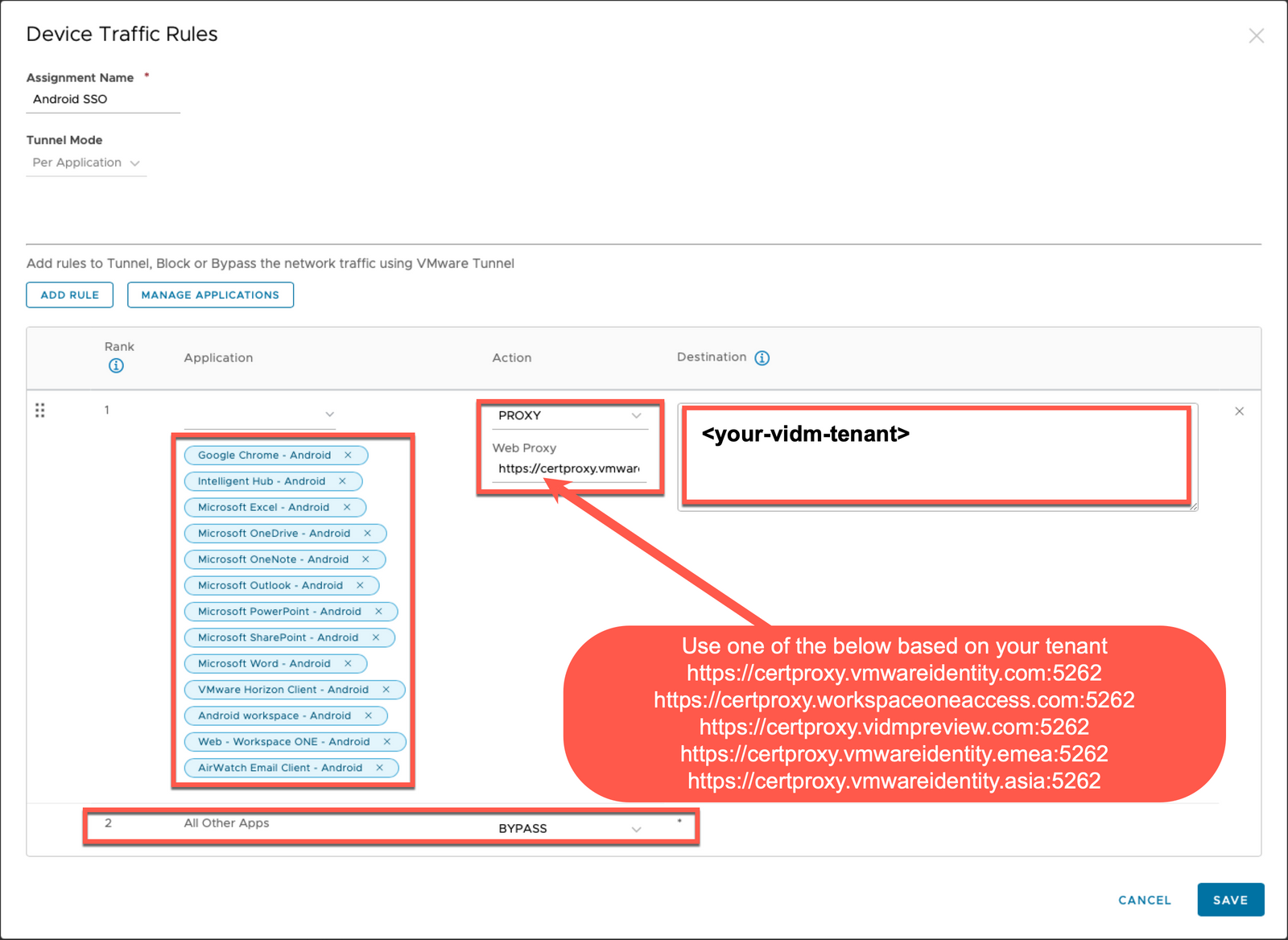
NOTE: In your DESTINATION settings, ONLY use FQDNs (don't add "HTTPS://" to the front of your Workspace ONE Access tenant). Adding the protocol to the front of the FQDN will break Android Mobile SSO for newer versions of Android. Older versions would still work.
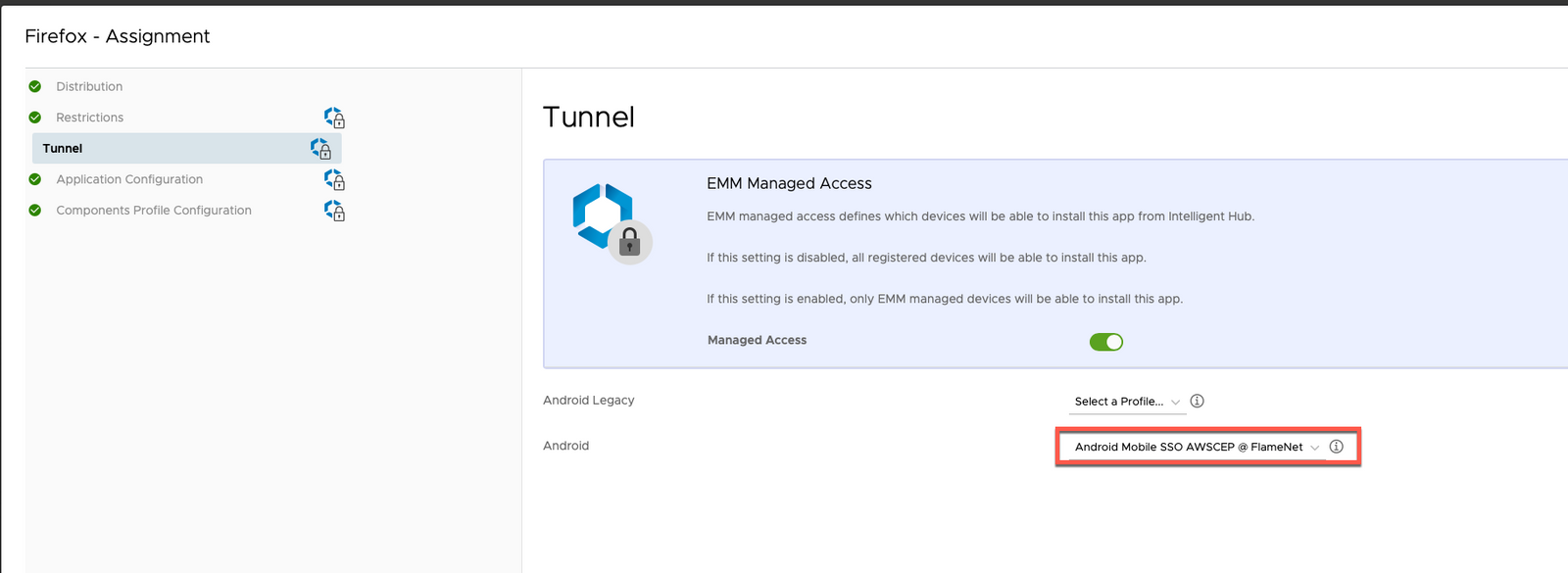
Edit Android Apps to Use Android SSO Profile (if needed)
- In Workspace ONE UEM, go to Resources -> Apps -> Native -> Public
- Edit each Android App Assignment Tunnel settings to use the Android SSO Profile
Edit the Android SSO Profile in Workspace ONE UEM to use Android SSO Traffic Rule
- In Workspace ONE UEM, go to Resources -> ProfilesEdit the Android SSO Profile you have defined above.
- Click ADD Version in the lower left
- Modify the Device Traffic Rules to use your Android SSO device traffic rule defined above.
- Click NEXT.
- Click SAVE & PUBLISH.
Testing
- When testing, first try to enroll the device by opening up Google Play store and downloading Workspace ONE Intelligent Hub. Once Hub is installed, launch it and authenticate (NOTE: If you have autodiscovery enabled, you can type in an organization email to determine the site info - otherwise you will need to manually type the server, OG, and user/pass/other credentials including MFA).
- Check the Tunnel app is installed. Open it and walk through the prompts (accept EULA, etc.). It should show DEVICE VPN CONFIGURED and INTERNET CONNECTED...but not show ENTERPRISE SERVER as connected (it will show disconnected if you DO NOT have VMware Tunnel with UAGs configured - This is ok as Mobile SSO won't use that as it is designed to proxy all Mobile SSO through the Tunnel app to your Workspace ONE Access / VMware Identity Manager tenant).
- Once authenticated via Hub, ensure enrollment continues and device is fully managed. You should see your profiles take place and apps load. Give it a minute or two to settle in.
- Once that is done, in order to test Mobile SSO properly, use Chrome within the Android Workspace (you configured it above) and browse to your Workspace ONE Access / VMware Identity Manager tenant. It should automatically sign you in.If not, you will see an "Access Denied" and need to troubleshoot.
Troubleshooting:
Check all of the settings defined above, specifically checking the following:
- Mobile SSO (for Android) Authentication Method in Workspace ONE Access Admin Console
- Mobile SSO (for Android) Policy Rule in Workspace ONE UEM - Specifically the Device Traffic Rules
- Android Profile in Workspace ONE UEM is defined to the device
- Each of the Android Apps are Configured to use Tunnel
- If necessary:
- Edit Android Apps to Use Android SSO Profile (if needed)
- Edit the Android SSO Profile in Workspace ONE UEM to use Android SSO Traffic Rule
- Unenroll and re-enroll the device
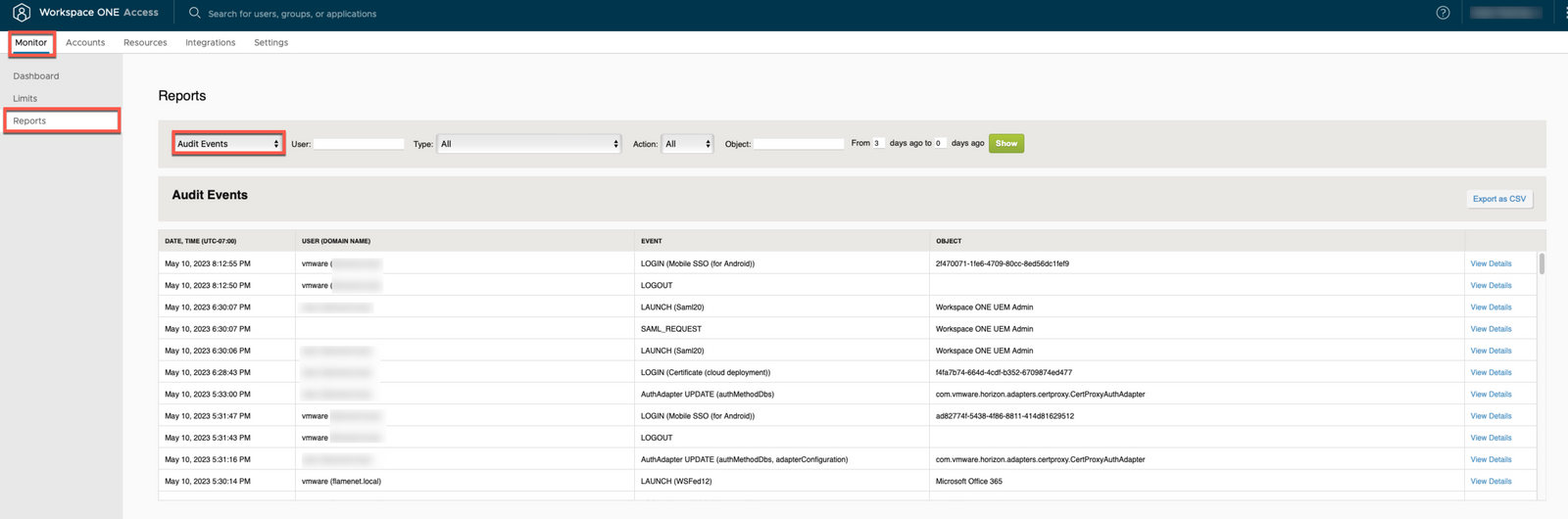
- The Workspace ONE Access admin console Audit Logs may provide some bit of information...make sure to click on the VIEW DETAILS on the right to see all the nitty-gritty stuff.
- If you see authentication failures without username, then the mobile sso configurations are incorrectly defined in the Mobile SSO (for Android) Authentication Adapter.
- If you see authentication failures with an unknown username, then the mobile SSO configurations regarding certificate template configurations are probably not correct (not gone over in this article) and likely the defined "username" (user principal name, user name, or email) are not properly defined within the certificate or being addressed in the Authenticator.